Bsports được biết đến là một trong những trang cá cược được nhiều người đánh giá cao. Số lượng người chơi đăng ký tài khoản trên hệ thống của nhà cái ngày càng gia tăng. Sản phẩm Bsport cung cấp cũng cực kỳ đa dạng và phong phú mang đến nhiều sự lựa chọn.
Giới thiệu tổng quan về Bsports cho người dùng
Bsports được biết đến là một trong những nhà cái cá cược online nổi tiếng nhất nhì tại khu vực châu Á. Bsports AC cung cấp đầy đủ các trò chơi được ưa thích hiện nay như cá cược thể thao, casino trực tuyến, xổ số, game bài, thể thao điện tử…
Bsports bongda chính là một trong những sản phẩm thế mạnh của nhà cái này. Trang chủ của nhà cái Bsports AI được thiết kế tường thuật trực tiếp toàn bộ trận đấu đang diễn ra. Người dùng dễ dàng xem được các trận đấu bóng đá thể thao trực tiếp vô cùng nhanh chóng.
Bsports cổng game hoạt động công khai và minh bạch có trụ sở chính đặt tại Philippines. Hệ thống nhà cái hoạt động đặt dưới sự quản lý của tổ chức Pagcor kiểm tra và giám sát chặt chẽ. Bsports hiện tại được quản lý bởi một công ty trực thuộc tại vương quốc Anh nên khá an toàn để tham gia cá cược.

Hệ thống nhà cái không ngừng theo đuổi công nghệ mới để mang đến trải nghiệm các sản phẩm cá cược chất lượng cao cho người dùng. Bsports sở hữu khả năng vận hành trò chơi mạnh mẽ cùng với chất lượng dịch vụ cao. Người chơi khi tham gia nhận được nhiều ưu đãi nổi bật về các sản phẩm chất lượng cao với tỷ lệ trả thưởng hấp dẫn.
Top các sản phẩm Bsports cung cấp nổi trội hiện nay
Bsports cung cấp đầy đủ và đa dạng với rất nhiều dòng sản phẩm cá cược khác nhau cho người dùng lựa chọn. Dưới đây là một vài sản phẩm nổi bật mà người chơi không nên bỏ qua trên hệ thống của nhà cái Bsports.
Thể thao Bsports
Thể thao Bsports chính là một trong những sản phẩm thế mạnh của hệ thống nhà cái nên được đầu tư khá mạnh mẽ. Sảnh cá cược độc quyền chứng minh được độ chịu chi của nhà cái về các sản phẩm này. Các sảnh thể thao của nhà cái đều có đội ngũ bình luận viên để hỗ trợ người dùng xem thể thao trực tuyến và cá cược. Tỷ lệ trả thưởng cho các sản phẩm cá cược thể thao cũng khá cao và nhiều chương trình khuyến mãi kèm theo cho người dùng.
Game Bsports
Game Bsports cực kỳ hấp dẫn với rất nhiều dòng game bài đỉnh cao cho người dùng lựa chọn. Người chơi khi tham gia dễ dàng đánh bài với nhau để kiếm thêm thu nhập tại nhà. Không khí cực kỳ vui nhộn với hệ thống âm thanh chất lượng cao không khác gì so với casino thực tế.
Xổ số Bsports
Xổ số Bsports cũng là một trong những sản phẩm vô cùng nổi bật trên hệ thống của nhà cái. Xổ số đầy đủ và đa dạng với nhiều trò chơi như xổ số ba miền, keno, bingo, xổ số nhanh…với giao diện cực kỳ đẹp mắt cùng với rất nhiều chương trình khuyến mãi ưu đãi.
Esport Bsports
Esport Bsports được thiết kế với giao diện cực kỳ bắt mắt và đầy đủ nhiều trò chơi hấp dẫn cho người dùng lựa chọn. Các trò chơi nổi bật như Liên Minh Huyền Thoại, Liên Quân Mobile, Dota2,…
Casino online Bsports
Casino online Bsports ngày càng thu hút người chơi bởi sự đa dạng và phong phú. Sảnh casino online được chia ra thành nhiều trò chơi như xóc đĩa, rồng hổ, bầu cua…dẫn dắt những game bài là những cô nàng vô cùng xinh đẹp và quyến rũ. Tỷ lệ trả thưởng casino cao và nhiều chương trình khuyến mãi hấp dẫn mang đến nhiều lựa chọn cho người dùng.
Slot game Bsports
Slot game Bsports cũng là một trong những trò chơi thu hút với số lượng người tham gia đông đảo. Các phiên bản Slot game đầy đủ và đa dạng với rất nhiều trò chơi hấp dẫn. Tỷ lệ trả thưởng cao với nhiều phần thưởng cộng dồn mang đến nhiều giá trị cho người chơi khi tham gia cá cược.
Hướng dẫn đăng ký tài khoản trên hệ thống Bsports nhanh chóng
Bsports nhà cái hỗ trợ người dùng đăng ký tài khoản vô cùng nhanh chóng và dễ dàng. Các bước sau đây sẽ hỗ trợ giúp cho bạn dễ dàng đăng ký tài khoản bằng số điện thoại di động hoặc bằng tài khoản.
Đăng ký bằng số điện thoại di động
- Người chơi chỉ cần truy cập vào đường link chính thức của nhà cái Bsports để đăng ký tài khoản. Bạn bấm vào nút đăng ký tài khoản và điền số điện thoại của mình để nhận mã xác minh.
- Người chơi điện đầy đủ tất cả những thông tin hiển thị và cài đặt mật khẩu đăng nhập tài khoản theo yêu cầu của nhà cái.
- Người chơi nên đặt tên cho tài khoản và xác nhận điều khoản mà hệ thống Bsports đưa ra.
- Bạn bấm vào nút hoàn thành đăng ký để tạo tài khoản mới cá cược trên hệ thống của nhà cái.
Đăng ký bằng tài khoản
- Bạn điền các thông tin được hiển thị sau đó nhập tên tài khoản và mật khẩu trên hệ thống Bsports.
- Bạn đặt biệt danh cho tài khoản cá cược của mình.
- Cuối cùng, bạn bấm vào nút đăng ký để hoàn tất việc tạo tài khoản cá cược.
Hướng dẫn nạp tiền Bsports chi tiết cho người dùng
Nạp tiền Bsports cực kỳ đơn giản và nhanh chóng thông qua thẻ ngân hàng. Các bước sau đây hướng dẫn cho bạn nạp tiền vào tài khoản để tham gia cá cược.
- Bạn chọn vào mục nạp tiền, lựa chọn Việt Nam đồng.
- Bạn chọn phương thức nạp tiền vào tài khoản của Bsports phù hợp.
- Người dùng lựa chọn số tiền cần nạp vào tài khoản sau đó điền đầy đủ tất cả những thông tin cá nhân cần thiết để hoàn tất bước này.
- Bạn bấm vào nút nạp tiền, cửa sổ khác hiện ra và bạn điền thông tin để thanh toán.
- Bạn sao chép số chuyển khoản cần phải trùng với số tiền giao dịch để tiến hành chuyển khoản vào tài khoản của nhà cái.
- Người chơi sau khi nạp tiền thành công, hệ thống nhà cái sẽ xuất hiện thông báo nạp tiền ở góc bên phải màn hình của trang.
Hướng dẫn rút tiền Bsports nhanh chóng và dễ dàng
Rút tiền Bsports cực kỳ đơn giản và không tốn quá nhiều thời gian của người dùng. Các bước sau đây hỗ trợ giúp cho người chơi rút tiền sau khi thắng cược nhanh chóng.
- Người chơi vào mục rút tiền, lựa chọn đồng Việt Nam trong danh sách tiền tệ và lựa chọn ngân hàng cũng như nhập tài khoản.
- Bạn nhập số tiền còn rút và lựa chọn phương thức rút tiền. Bạn bấm vào nút rút tiền để thực hiện rút tiền về tài khoản của mình.
- Bạn tiến hành nhập mã xác minh để được gửi về điện thoại trong vài giây.
- Người chơi lựa chọn xác nhận và chờ chuyển khoản từ phía Bsports.
Cách tải Bsports app cho người chơi nhanh chóng trên điện thoại
Hướng dẫn Bsports cách tải app trên điện thoại vô cùng đơn giản và nhanh chóng. Tải Bsports app giúp bạn trải nghiệm các sản phẩm cá cược trên điện thoại hệ điều hành Android và iOS dễ dàng. Tải Bsports cực kỳ đơn giản với những bước hướng dẫn sau đây.
- Bạn chỉ cần truy cập vào đường link chính thức của nhà cái Bsports đợi download ứng dụng.
- Người dùng lựa chọn mục tải ứng dụng hiển thị trên trang chủ Bsports để download ứng dụng. Bạn lựa chọn quét mã QR app hỗ trợ cho điện thoại Android hoặc iOS.
- Màn hình cửa sổ hiển thị, bạn chỉ cần sử dụng thiết bị di động của mình để quét mã QR hiện ra.
- Hệ thống gửi yêu cầu xác nhận truy cập từ nguồn đáng tin cậy, bạn bấm vào nút “Yes” và chờ đợi quá trình tải app Bsports trên điện thoại thông minh của mình.
Tổng hợp các chương trình khuyến mãi hấp dẫn của Bsports
Khuyến mãi Bsports cực kỳ đa dạng và phong phú mang lại nhiều lựa chọn cho người chơi khi tham gia. Dưới đây là những chương trình khuyến mãi hấp dẫn trên hệ thống của nhà cái để người chơi tham khảo lựa chọn.
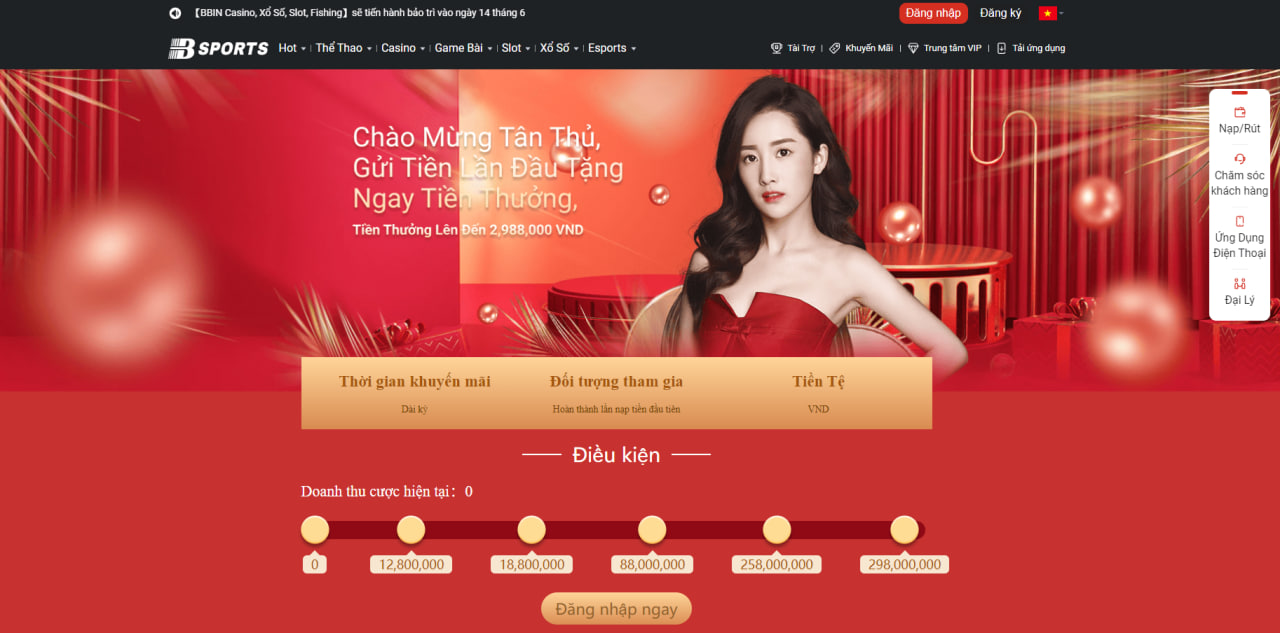
Chào mừng tân thủ mới
Bsports ưu đãi dành cho mỗi thành viên khi nạp tiền lần đầu tiên nhận được số tiền trị giá lên đến 2.988.000 đồng. Số tiền người chơi nạp vào tối thiểu là 50k có cơ hội nhận về những phần thưởng tương ứng.
Tỷ lệ hoàn trả
Bsports thiết kế chương trình hoàn trả vô cùng hấp dẫn dành cho người chơi khi tham gia cá cược. Anh em khi tham gia cá cược có mức hoàn trả cao nhất là 1.2%, số tiền đạt là 299.880.000 đồng.
Bảo hiểm tiền cược
Nếu như người chơi tham gia cá cược không may mắn có chương trình hoàn trả tiền cược. Số tiền mà người chơi nhận được lên đến 29.980.000₫. Đây là một trong những chương trình khuyến mãi hấp dẫn dành cho anh em có thêm vốn để tham gia cá cược nếu như bị thua.
Đặc điểm nổi trội của hệ thống nhà cái Bsports
Bsports được đánh giá là một trong những hệ thống nhà cái vô cùng uy tín và chuyên nghiệp với rất nhiều tính năng nổi trội. Những tính năng nổi trội của hệ thống nhà cái thời gian gần đây phải kể đến như.
Tin tức Bsports
Tin tức Bsports cung cấp đầy đủ tất cả những thông tin hấp dẫn để hướng dẫn người chơi tham gia cá cược. Chia sẻ một vài kinh nghiệm cũng như bí quyết giúp người chơi nâng cao khả năng chiến thắng khi tham gia cá cược trực tuyến. Đây được biết đến là một trong những tính năng mới của Bsports mà không phải hệ thống nào cũng cung cấp được.
Soi kèo Bsports
Soi kèo Bsports cung cấp đầy đủ đa dạng nhiều loại kèo khác nhau để người chơi tham khảo. Tất cả những loại kèo đều được chuyên gia lâu năm trong lĩnh vực cá cược nhận định. Đây được biết đến là một trong những nguồn thông tin vô cùng hữu ích để giúp cho người chơi tham khảo và đưa ra lựa chọn đặt cược phù hợp.
Bsports live
Bsports live thường xuyên và trực tuyến trên trang web của họ để cung cấp nhiều mã khuyến mãi cho người chơi. Đây là một trong những cơ hội giúp người chơi lựa chọn để nâng cao lợi ích khi tham gia cá cược. Ngoài ra, Bsports cung cấp tính năng này để giúp người chơi có thể tương tác được với nhà cái cũng như những cô nàng xinh đẹp quyến rũ hỗ trợ cá cược.
Lý do vì sao Bsport lại được lòng người chơi tại Việt Nam?
Bsports được đánh giá là một trong những thương hiệu vô cùng uy tín và chuyên nghiệp để người chơi lựa chọn tham gia cá cược. Dưới đây là những nguyên nhân khiến cho hệ thống nhà cái nhận được sự tin tưởng của người chơi khi tham gia đăng ký tài khoản và kiếm tiền tại nhà.
Giao dịch nhanh chóng
Bsports được nhiều người đánh giá cao bởi giao dịch nạp tiền vào rút tiền cực kỳ nhanh chóng và uy tín. Hệ thống nhà cái xây dựng đa dạng với rất nhiều phương thức khác nhau để hỗ trợ cho người chơi trong vấn đề nạp tiền và rút tiền. Các phương thức nạp tiền và rút tiền đa dạng cũng như hỗ trợ người chơi vô cùng nhiệt tình. Hệ thống bảo mật thông tin cực kỳ tốt tránh tình trạng lộ thông tin của người dùng khi tham gia cá cược.
Giao diện đơn giản
Bsports thiết kế giao diện vô cùng đơn giản và đẹp mắt để giúp người chơi dễ dàng tương tác. Hình ảnh đồ họa và âm thanh trên hệ thống nhà cái nổi bật mang đến nhiều trải nghiệm tuyệt vời cho người dùng.
Chăm sóc khách hàng chu đáo
Bsport xây dựng bộ phận chăm sóc khách hàng vô cùng chu đáo để hỗ trợ người dùng. Hệ thống nhà cái triển khai đa kênh để giúp cho người chơi gặp khó khăn có thể chủ động liên hệ nhanh chóng. Các phương thức hỗ trợ người chơi nhanh chóng và tận tình để giúp cho anh em dễ dàng hơn trong việc liên hệ khi gặp khó khăn.
Nhiều sản phẩm
Bsports cung cấp khá đầy đủ và đa dạng với rất nhiều sản phẩm cá cược cho người chơi trải nghiệm. Tất cả các sản phẩm cá cược đều vô cùng hấp dẫn và phù hợp với xu thế hiện nay của thị trường. Tỷ lệ trả thưởng cao và rất nhiều chương trình khuyến mãi dành cho các sản phẩm cá cược trên hệ thống của nhà cái. Người chơi dễ dàng lựa chọn được các sản phẩm phù hợp với mình để tham gia kiếm tiền tại nhà.
Bảo mật tốt
Bsports cổng nhà cái game cá cược uy tín hàng đầu Việt Nam ứng dụng công nghệ bảo mật hàng đầu trên thế giới. Người chơi khi tham gia không cần lo lắng về vấn đề lộ thông tin ra bên ngoài khi cá cược. Tất cả những thông tin của người chơi đều được mã hóa an toàn để đảm bảo mang đến sự an tâm cho người dùng. Thông tin của người chơi được lưu trữ tại hệ thống nước ngoài và được đội ngũ nhân viên kỹ thuật kiểm tra hàng ngày.
Nhiều chương trình khuyến mãi
Bsports phát triển đầy đủ và đa dạng với rất nhiều chương trình khuyến mãi để người chơi lựa chọn tham gia. Các chương trình khuyến mãi vô cùng hấp dẫn, thu hút người dùng. Dù bạn là người chơi mới hay người chơi lâu năm vẫn dễ dàng nhận được ưu đãi từ phía nhà cái.
Hỗ trợ ứng dụng
Bsports app tương thích cho hệ điều hành Android và iOS để người dùng dễ dàng download trên điện thoại thông minh. Người chơi sử dụng điện thoại hệ điều hành gì vẫn có thể dễ dàng download ứng dụng của nhà cái để trải nghiệm các sản phẩm cá cược. Ứng dụng cũng không có gì khác biệt so với phiên bản website để người chơi tham gia cá cược dễ dàng và nhanh chóng.
Bsports có uy tín để tham gia cá cược hay không?
Bsports đáp ứng đầy đủ tất cả những tiêu chí của một hệ thống nhà cái uy tín và chuyên nghiệp trên thị trường hiện nay. Người chơi hoàn toàn an tâm đăng ký tài khoản và trải nghiệm các sản phẩm cá cược trên hệ thống của nhà cái.
- Hệ thống nhà cái có nguồn gốc xuất xứ rõ ràng và có giấy phép kinh doanh hợp pháp từ tổ chức Pagcor. Đây là một trong những yếu tố vô cùng quan trọng để đánh giá sự chuyên nghiệp và uy tín của nhà cái.
- Bsports xây dựng quy trình nạp tiền và rút tiền nhanh chóng để người chơi không cần lo lắng về vấn đề này. Tốc độ xử lý nạp tiền, rút tiền nhanh chóng và chưa có trường hợp nào không thể rút tiền được từ phía nhà cái nếu hợp lệ.
- Hệ thống bảo mật thông tin chất lượng cao ứng dụng công nghệ hàng đầu để tránh tình trạng thông tin bị lộ ra bên ngoài. Bsports quy định nhiều điều khoản về vấn đề bảo mật thông tin và bắt buộc tất cả những tài khoản tham gia cá cược đều phải tuân thủ.
- Dịch vụ chăm sóc khách hàng đỉnh cao hỗ trợ người chơi 24/7 bất cứ khi nào cần. Nếu người chơi gặp khó khăn chỉ cần chủ động liên hệ thông qua đa kênh là được hỗ trợ nhanh nhất.
- Bsport nhận được sự phản hồi và đánh giá vô cùng tích cực của rất nhiều người chơi cá cược trên thị trường hiện nay. Một số đơn vị hiện nay giới thiệu hệ thống nhà cái cho người chơi khi muốn tìm kiếm một đơn vị uy tín và chuyên nghiệp.
Kết luận
Bsports xứng đáng trở thành một trong những hệ thống nhà cái uy tín và chuyên nghiệp trên thị trường hiện nay cho người dùng Việt Nam. Thông qua những thông tin đánh giá về hệ thống nhà cái thông qua các mặt mong muốn mang đến cho người chơi cái nhìn tổng quan. Người chơi đưa ra lựa chọn phù hợp để kiếm thêm thu nhập tại nhà bằng hình thức cá cược trực tuyến.
Thông qua những thông tin chia sẻ về hệ thống nhà cái Bsports mong muốn anh em có thêm nhiều gợi ý về đơn vị uy tín và chuyên nghiệp trên thị trường. Nếu yêu thích nhà cái đừng quên đăng ký tài khoản để trải nghiệm các sản phẩm chất lượng cao.
